There are many scenarios that we can control with Azure Policy. In fact, we can generate all the combinations that we want as it is a service that allows you to define your own rules. Today I wanted to share with you one that I have created to restrict the purchase from the Azure Marketplace.
How to define the policy
To know what to include in the policies, you usually have to rely on the fields that a resource has in its ARM template. The easiest way to see these fields is by using the Azure Resource Explorer service.
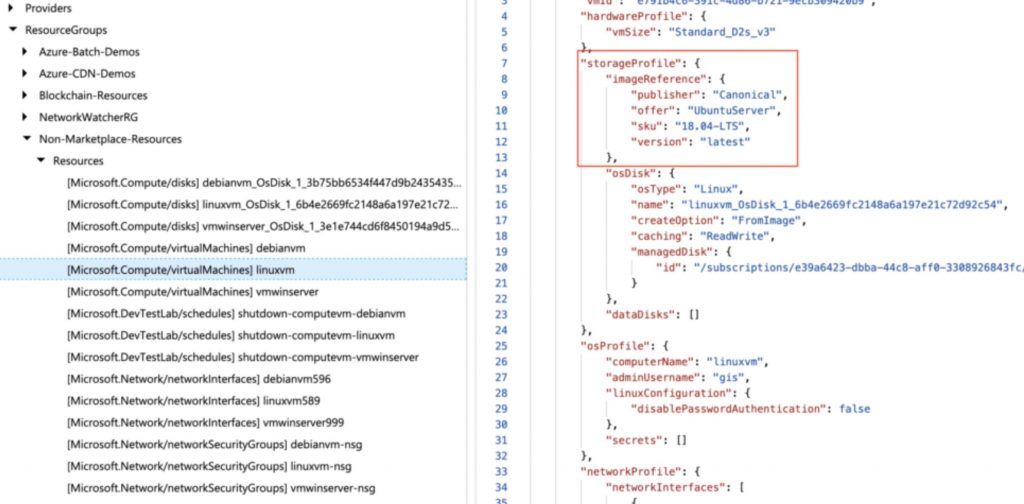
In this case I am going to use the publisher field that will tell me who is the one that published the virtual machine.
Policies look like this:
{
"mode": "All",
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"in": [
"Microsoft.Compute/disks",
"Microsoft.Compute/virtualMachines",
"Microsoft.Compute/VirtualMachineScaleSets"
]
},
{
"not": {
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"in": [
"Microsoft",
"MicrosoftWindowsServer",
"Microsoft-AKS",
"Canonical"
]
}
]
}
}
]
},
"then": {
"effect": "audit"
}
},
"parameters": {}
}The first thing I do is check that the type of resource is a virtual machine and the second that it does not have as publisher any of those that I indicate, which are the machines outside the Marketplace. I recommend that the effect initially be of the audit type, to verify that the results are correct. Once you verify that it is working you can change it to deny status.
